The Rundown
Despite global uncertainty from tariffs, wars, and a government shutdown, venture capital activity in Q3 showed surprising strength. Unsurprisingly, this strength was mainly driven by immense interest in artificial intelligence. Investors are concentrating larger sums into fewer, more ambitious startups, pushing valuations higher while maintaining selective deal flow.
Once again, we look under the hood to make sense of the quarter’s cybersecurity investment data, providing unique analysis and insights into the areas of cybersecurity investment that are making the greatest impact.
Q3 2025 – AI Driving Valuations Sky-High
Early-stage venture capital is climbing from the lows of 2024 as investors write eye-watering checks for AI startups. As we will discuss in our analysis, cybersecurity has not only moved in step with this trend, but it has also occasionally led it. The question that remains is how long AI enthusiasm can sustain these elevated valuations before the market cools.
From AI to Identity: Cyber M&A Continues Into Q3
Cybercriminals are using AI to attack at speed and at scale. For larger companies, often the best way to keep pace with this evolution is to buy innovations. Q3 saw two major deals: Palo Alto Networks’ acquisition of identity security company CyberArk, and SentinelOne’s acquisition of Observo AI. We examine the factors that led to these deals and how companies are using M&A to retain their competitive edge in the AI age.
The Day the Cat Stalled: How Jaguar Land Rover’s Cyber Attack Became a Supply Chain Parable
In September, the cyber and business communities shared a collective gasp when a cyberattack accomplished what no recession, pandemic, or labor strike ever could – Jaguar Land Rover was forced to stop production for several weeks. The crisis is perhaps the starkest example of how cyber risk has become a boardroom issue that can threaten a company’s reputation, investor confidence, and even national economies.
Why We Stopped Tuning and Started Coding: The Engineering Revolution in Detection
The rise of Detection Engineering best encapsulates cybersecurity’s shift from reactive defense to proactive engineering. But another shift is underway. In this section, we examine how an organization’s ability to standardize its security logic through Detection-as-Code will be the most critical factor in determining how effectively it can adopt and leverage future autonomous AI defense mechanisms.
A Phish, a Worm, and One Very Bad npm Week
In September 2025, two major npm supply-chain attacks exposed serious weaknesses in open-source security. The first involved an account compromise that infected 18 popular npm packages, while the second was a self-replicating worm that spread through build systems and GitHub Actions.
Software supply-chain attacks have been a serious threat for many years, but these examples show the next threat level: attackers are abusing collaboration and automation themselves.
Introduction
In Q3, venture capital kept climbing a wall of worry. Tariff tensions, armed conflicts, and the current ongoing government shutdown should all be weighing on the global economy, yet early-stage investing has refused to slow. Beneath that resilience lies a massive technological shift—from a structured, deterministic-compute driven digital world to one powered by artificial intelligence. This transformation has made AI not only the gravitational center of the venture market and the catalyst for a new wave of cyber innovation, but also an increasingly suspected sole force behind the momentum of the broader global economy.
The data tells a story of contrast. Deal volumes are recovering but remain controlled, even as valuations push to new highs. Investors are concentrating their bets with larger checks flowing into fewer, more technically ambitious startups. Cybersecurity continues to track this momentum closely, often leading the market on valuation multiples and strategic exits. The tension between exuberance and selectivity defines this cycle: capital is abundant for founders who can harness AI or solve emerging risks created by it.
Those same dynamics are reshaping the cyber M&A landscape. Q3 saw major moves like Palo Alto Networks’ $25B acquisition of CyberArk and SentinelOne’s purchase of Observo AI, signaling how identity and data are becoming the control planes of the AI era.
Also during the quarter, cyber challenges and learnings continued. The Jaguar Land Rover breach reminded executives and investors alike that cyber resilience is now a board-level metric, not an IT concern. In parallel, the open-source ecosystem faced its own reckoning, as npm supply-chain attacks revealed how fragile trust and automation have become.
Q3 State of the Market – Cyber Deal Activity
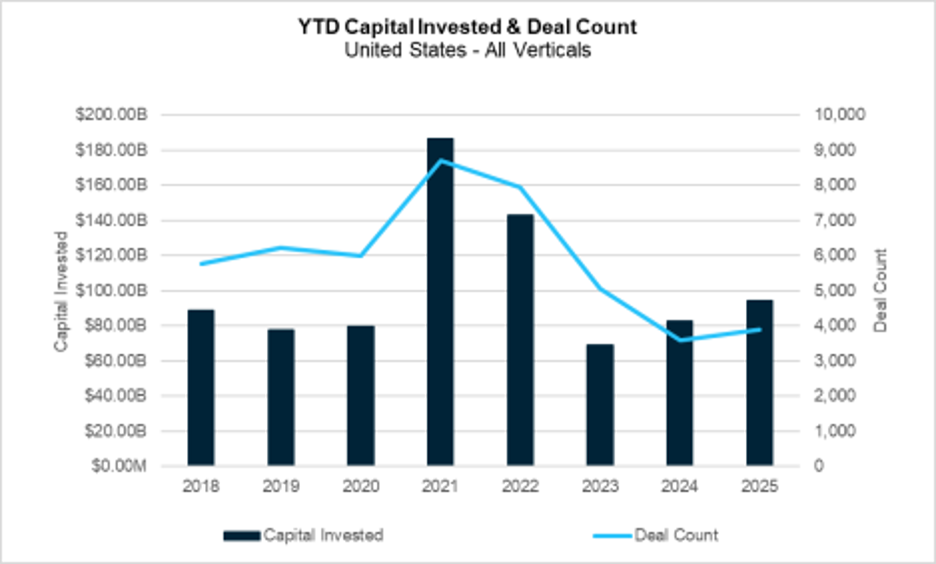
Despite tariff wars, real wars, and even government shutdowns, early-stage venture capital continues to climb from the lows of 2024. As we will discuss in our analysis, what we once described as a flight to quality has evolved into a flight to AI. The excitement around applying artificial intelligence across every corner of technology seems to have buoyed investment activity. We posit it has also contributed to a relentless rise in early-stage valuations. Cybersecurity has moved in step with this trend, and in some cases, has led it. The question now is how long AI enthusiasm can sustain these elevated valuations before the market cools.
The following chart highlights the trend. Deal volume in 2025 remains above last year’s trough. In addition, capital invested, which bottomed earlier in 2023, has accelerated even faster. The divergence between deal count and capital flow hint that valuations continue to climb.
Continued Recovery in the Venture Market
Source: PitchBook
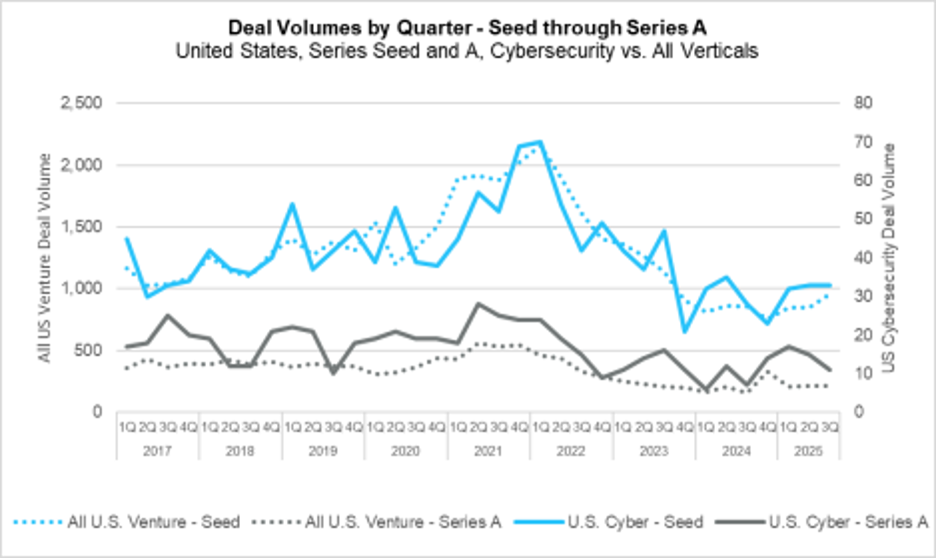
In the following chart, we see that despite a modest uptick in seed deal volume this quarter, activity remains within the sub-1,000 range that has persisted since the post-2022 slowdown. Series A deal volume overall was flat, while cybersecurity Series A activity declined slightly but remained above 2024 levels. This combination of subdued deal volume, rising valuations (discussed later), and increased capital investment points to a clear trend that investors are becoming more selective, directing larger checks to a smaller group of companies.
Volume Recovering Even as Prices Soar
Source: Pitchbook
While the government shutdown delayed the release of September data on high-propensity business registrations, July and August figures showed a continued upward trend in new company formation. Product launches, a leading indicator of early-stage deal flow, remained steady and roughly in line with pre-pandemic levels. The combination of rising business registrations, flat deal activity, and steady product launches suggests that investor selectivity remains high and is likely to persist as more founders enter the market.
While 2021 and 2022 marked a surge in overall venture capital activity, the AI boom began later, gaining real momentum a few quarters after the launch of ChatGPT in 2022. The following chart illustrates how AI came to dominate venture investing after that point. As shown in the chart below, enthusiasm around AI reached new highs this quarter, with 48.6 percent of all deals occurring in the sector, according to PitchBook. These deals represented 58 percent of capital investment during the same period. This gap between capital investment and deal volume also suggests that AI companies are commanding premium valuations. This surge in AI activity has influenced cybersecurity as well, where valuations are rising faster than the broader market, a trend explored further in the next section.
AI Takes Over Venture Investing
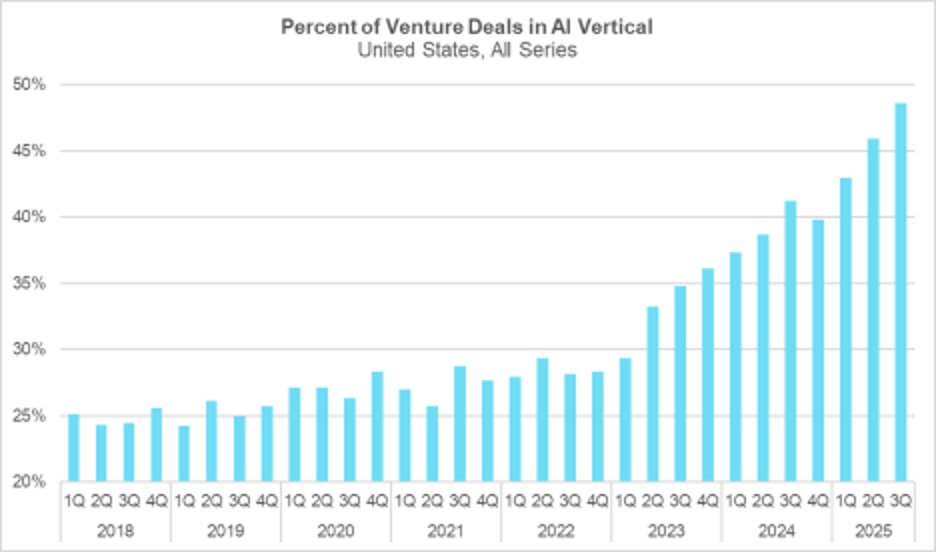
Source: PitchBook
The following chart shows that early-stage valuations continued to climb in Q3, with median pre-money values in the broader market now exceeding their 2022 highs at Series A. Cybersecurity valuations also strengthened, once again exceeding the overall market average during the quarter. Seed-stage valuations continued their upward climb, with the broader market reaching more than double its 2018 median. At both the seed and Series A stages, cybersecurity outperformed the broader market, with seed valuations reaching nearly 250 percent of their 2018 levels.
Overall, the data supports the view of a flight to quality, as investor interest concentrates in select verticals such as cybersecurity, pushing valuations higher. This trend is not universal, however, and the next section examines companies raising capital from a weaker position.
Early Stage Valuations Climb Further
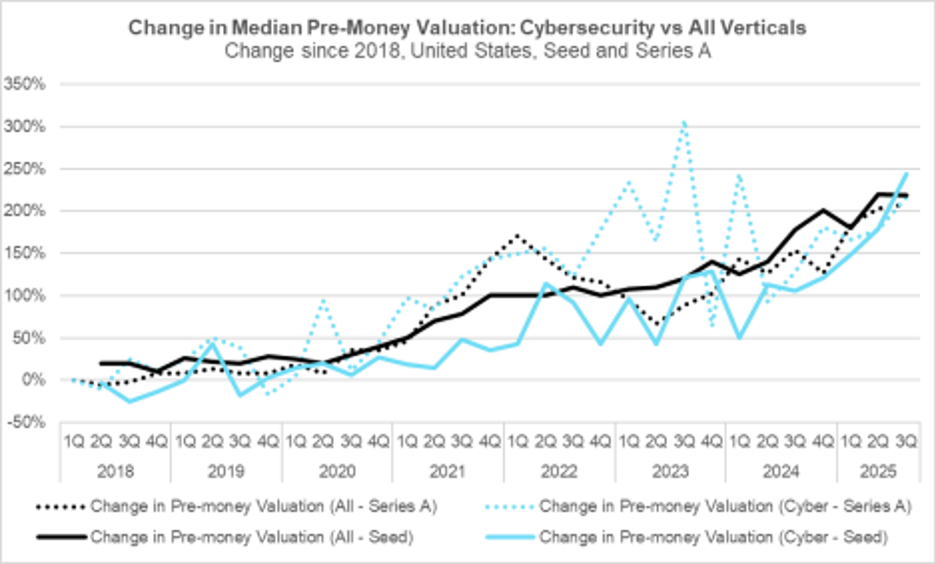
Source: PitchBook
In the chart below, Q3 down rounds remained at the elevated levels seen throughout 2023 and 2024, continuing the trend from the previous quarter. When combined with flat rounds, they held steady around the 10 percent mark that has characterized the post-pandemic venture landscape.
Across the broader market, step-ups hovered near the 2x level where they have stayed since early 2023. Cybersecurity, however, showed modest gains, with median step-ups reaching 2.71x during the quarter. Although data for the cybersecurity vertical can be more volatile due to lower deal volume, the combination of rising step-ups and record-setting seed valuations suggests that a correction may be coming. The question now is whether cybersecurity seed valuations will return to more sustainable levels, or if Series A valuations will climb back toward their 2023 highs.
Down Rounds Remain Elevated at Series A

Source: PitchBook
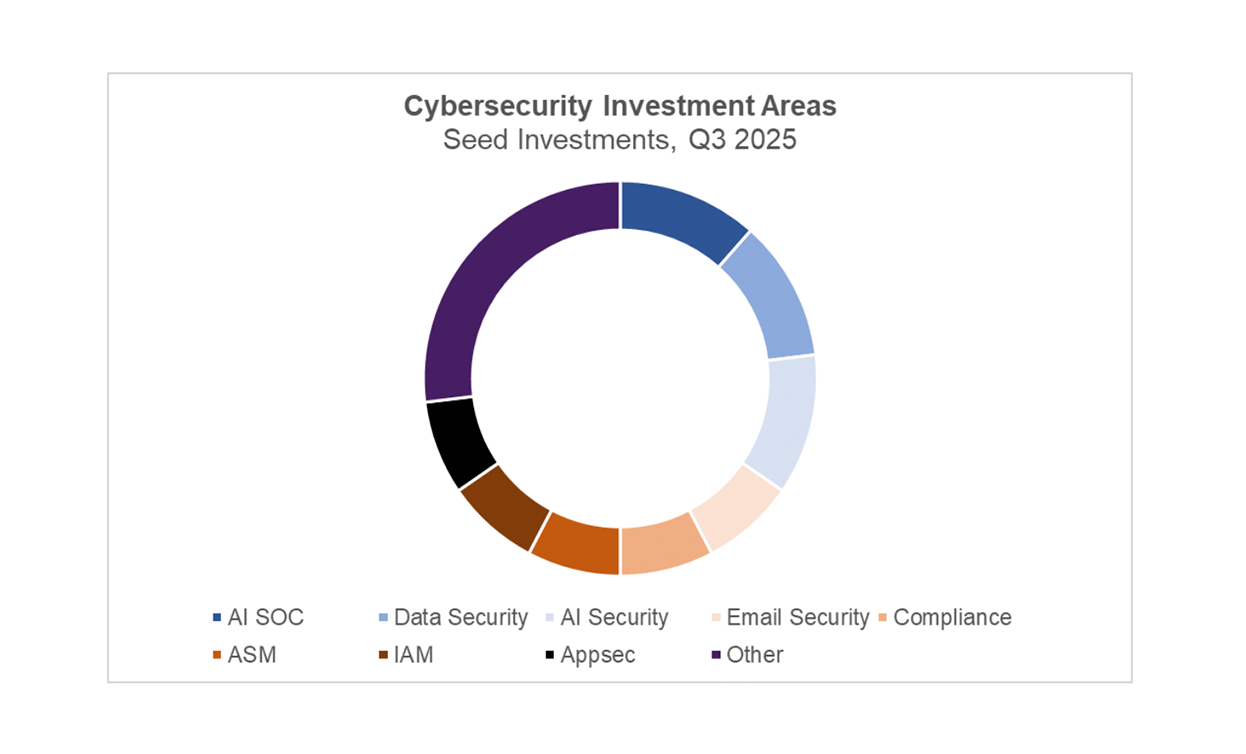
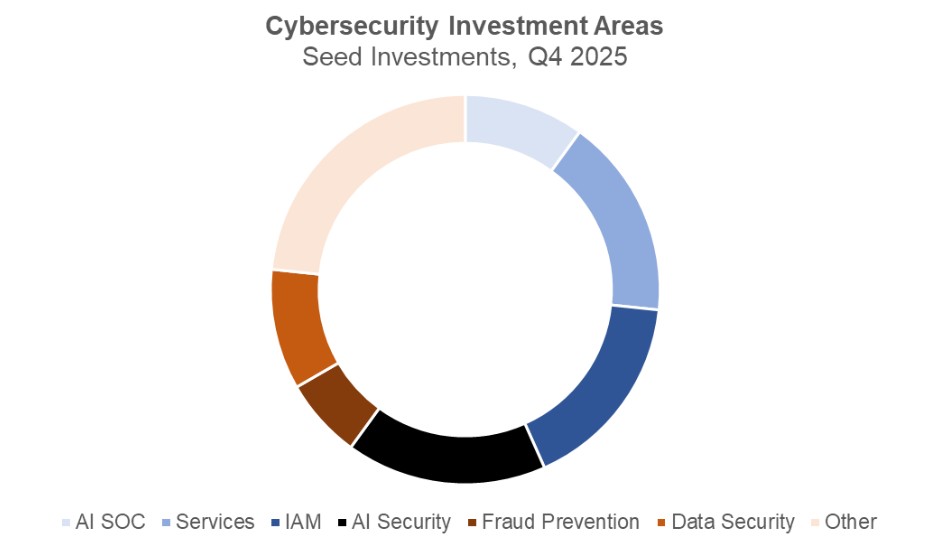
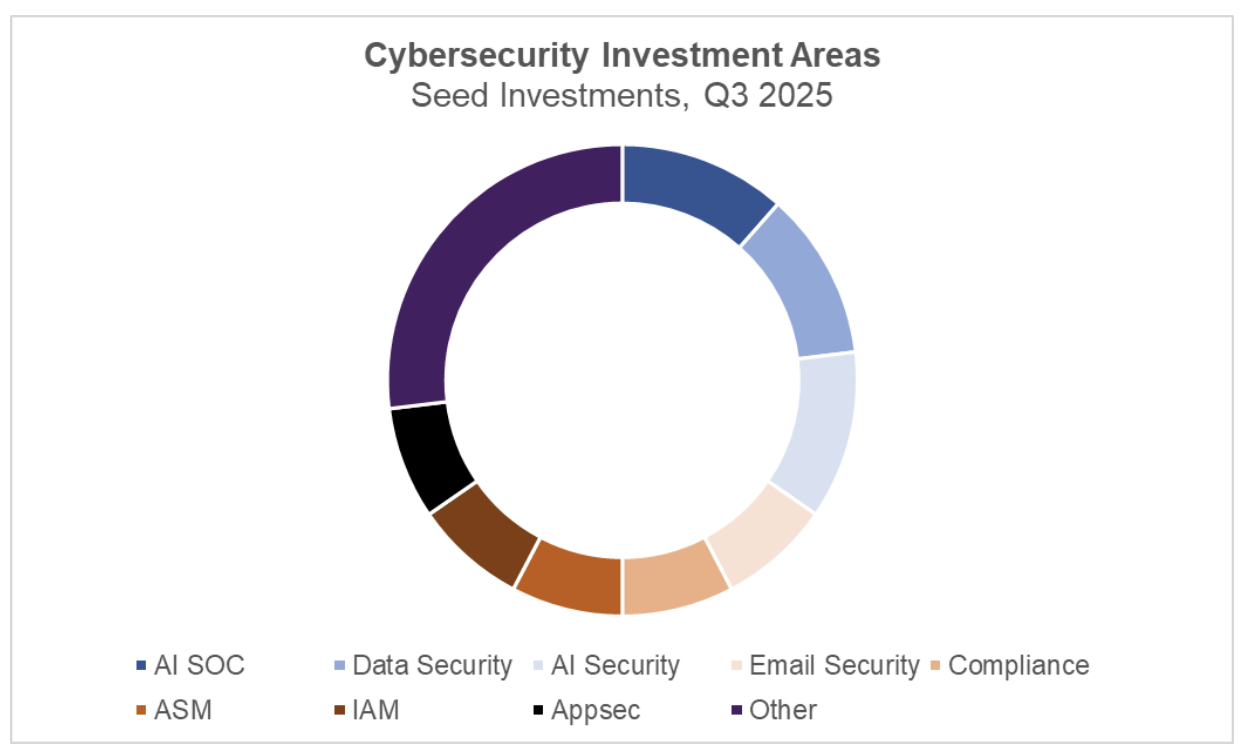
In previous quarters, investors concentrated on companies using AI to automate tasks traditionally performed by humans. AI “employees” were being built to investigate alerts in the SOC, red-team applications and networks, and identify or remediate code vulnerabilities. This quarter, the data in the chart below tells a different story. Investors directed capital toward companies betting that AI can deliver step-change improvements in areas already served by established cybersecurity tools. Categories such as email security, DSPM, endpoint protection, and training accounted for nearly 30 percent of both deal volume and capital invested during the quarter.
Another major driver of investment was AI Security, which this quarter showed a stronger focus on protecting the security and identity of AI agents themselves. Although these companies represented just under 20 percent of deals, they captured nearly 43 percent of total capital invested.
Old Problems are New Again
From AI to Identity: Cyber M&A Continues Into Q3
Cybersecurity has always been fueled by M&A. Once platform players like CrowdStrike or Palo Alto Networks hit scale, organic growth alone can’t keep up with an environment defined by fast-moving adversaries and an ever-expanding attack surface. The only way to stay ahead is to buy innovation.
Part of the story is structural. Over the past two decades, regulations and market sentiment have pushed IPO thresholds higher, making it harder for startups to go public at a modest scale. The result: a steady cycle where large public companies snap up emerging innovators, and where those startups often find it more rational to sell than spend years chasing the size now required to publicly list.
According to strategic advisory firm Altitude Cyber, the sector saw extreme variation in both deal count and value over recent years. The high‑water mark arrived during the six quarters from Q1’21 through Q2’22, an era buoyed by easy capital, when roughly 430 transactions totaled about $115.9B. Activity slowed materially in the following period as rates rose and valuation expectations reset.
A Look At How M&A Activity Has Evolved Since 2018
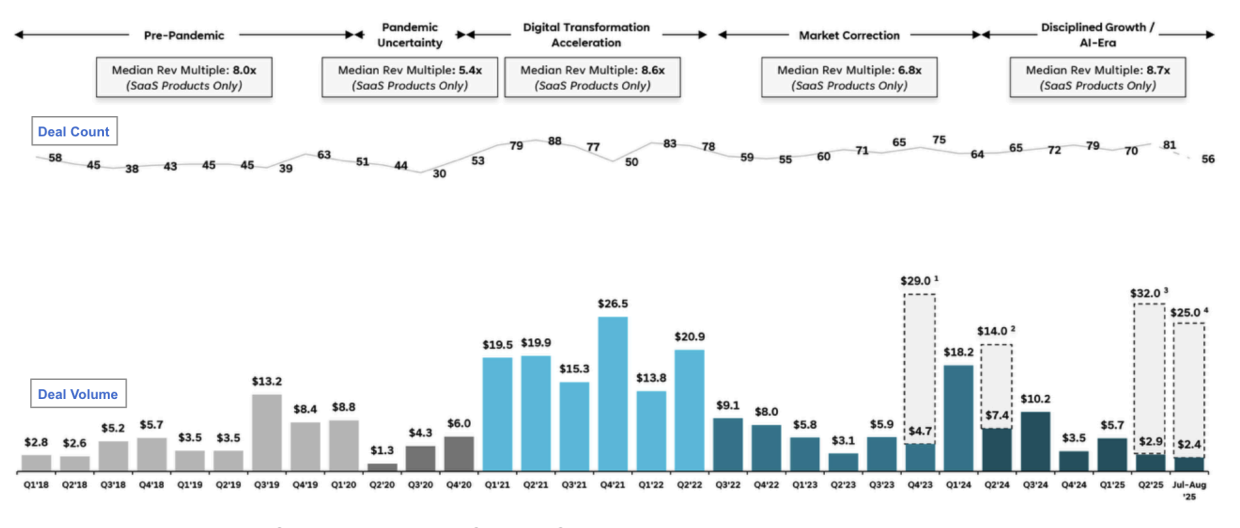
Source: Altitude Cyber: Cybersecurity Market Review 2025
That context brings us to 2025. Momentum that began to rebuild in 2024 accelerated again in Q3 ’25, with increases in both deal count and total value. The driver isn’t new, but its urgency is: AI is now everywhere. As enterprises operationalize AI across workflows, a new class of risks joins the classic vectors. LLMs, inference pipelines, retrieval layers, and agentic systems introduce identities that don’t behave like people, data flows that don’t fit legacy guardrails, and telemetry volumes that strain traditional analytics. Security leaders are responding with both roadmaps and acquisitions. Let’s take a closer look at two Q3 deals and how they map to these themes.
Palo Alto Networks Acquires CyberArk for ~$25B
In August, Palo Alto Networks announced an agreement to acquire CyberArk for roughly $25B, adding market‑leading identity security (IAM/PAM) to its platform. With CyberArk’s 2024 revenue around $1B, the implied multiple is approximately 25×, a premium consistent with scarce, category‑defining assets.
While the transaction clearly strengthens Palo Alto’s core feature set, it also positions the company for the identity challenges of AI. As autonomous and semi‑autonomous agents proliferate, they require credentials, roles, and policy controls that aren’t designed for human users. Machine identities, service accounts, secrets management, and least‑privilege enforcement become table stakes across model development, inference, and agent orchestration. CyberArk brings a proven spine for managing privileged access and machine‑to‑machine trust at enterprise scale, capabilities that will only grow more critical as AI systems move from pilot to production.
Strategically, the deal also reduces platform friction for customers pursuing “consolidate‑to‑quality” vendor strategies. Identity is the connective tissue across network, endpoint, cloud, and data controls; tighter integration should translate to simpler deployments, stronger detections, and faster time to value. Expect Palo Alto to lean into cross‑sell motions and to use CyberArk’s depth to differentiate in zero‑trust and agent‑safe architectures.
SentinelOne Acquires Observo AI for ~$225M
Smaller in absolute dollars but squarely on trend, SentinelOne’s acquisition of Observo AI highlights how leaders are buying data‑plane leverage. Observo automates the movement and transformation of security data, ingesting logs and events at scale, enriching in real time, applying detections, and routing to the right destinations efficiently.
AI is hungry for high‑quality, well‑labeled telemetry. Models and detections only perform as well as the data pipelines that feed them. By bringing Observo in‑house, SentinelOne aims to reduce customers’ ingestion costs, improve time‑to‑signal, and enable more advanced analytics across sprawling cloud, identity, and application footprints. In practical terms, that means better visibility for both AI‑assisted threat hunting and automated response, with less operational drag on data engineering teams.
Thematically, Observo sits at the intersection of two secular shifts: (1) security data is expanding faster than budgets, making “smarter, cheaper” pipelines a must‑have, and (2) AI‑centric workflows amplify the value of normalized, enriched, and privacy‑aware telemetry. Expect more tuck-ins here, including data transformation, lineage, labeling, and privacy-preserving tools that make AI in security both powerful and governable.
Driven by AI’s demands and opportunities, cyber M&A is pushing back toward the heights of 2021–2022. The strategic logic is straightforward: identity becomes the control plane for AI‑era architectures, and telemetry becomes the fuel. Big, identity-centric platform deals will dominate headlines. Most other transactions will look more like Observo, focused on giving incumbents the data advantages and integration paths their customers now require.
As organizations scale AI from experiments to mission‑critical systems, they will reward platforms that can (1) prove who—or what—should have access, (2) observe and enrich data flows at line rate, and (3) translate those signals into automated, auditable controls. M&A remains the fastest way for leaders to close those gaps. Given the pipeline of venture‑backed innovation and the breadth of buyers, ranging from public platforms to private‑equity rollups, the pace is likely to persist into 2026.
The Day the Cat Stalled: How Jaguar Landrover’s Cyber Attack Became a Supply Chain Parable
In September 2025, a cyberattack accomplished what no recession, pandemic, or labor strike ever managed. It brought Jaguar Land Rover (JLR) to its knees. The British luxury automaker, owned by Tata Motors, was forced to halt production around the world for several weeks.
This incident went far beyond a technical failure. It became a wake-up call that exposed how deeply modern manufacturing depends on fragile digital systems. When software connects every factory, supplier, and logistics partner, one breach can ripple through an entire enterprise and freeze global operations.
JLR’s experience revealed a hard truth. Cyber risk has become a boardroom issue that can threaten a company’s reputation, investor confidence, and even national economies.
The trouble started on August 31, 2025, when JLR’s global IT systems went haywire. The company’s immediate response was to shut everything down to limit the damage. But by the next morning, factories in the UK, India, China, and Slovakia were silent.
Executives called it a “cyber incident,” which was a polite way of saying the company had completely ground to a halt. Supply chains froze, dealer websites went dark, and thousands of half-built cars sat idle on production lines. Employees were told to stay home. Analysts later put the cost at about £50 million in lost output every single week.
A few days later, a hacker group calling themselves “Scattered Lapsus$ Hunters” claimed responsibility on Telegram, posting screenshots of JLR’s internal files as proof. The name was a mix of three infamous gangs, which made investigators think it was a clever rebrand more than a formal merger. Whatever their true identity, they had done it: they had digitally paralyzed one of Britain’s largest manufacturers.
At first, JLR said there was “no evidence of data exfiltration.” Two weeks later, they changed their tune, admitting that some internal and supplier data had been “affected.” By then, the damage had spread far beyond JLR. Small suppliers, who were already on tight budgets, suddenly weren’t getting paid. Some had to take out personal loans to stay afloat.
As losses grew, the UK government intervened with a £1.5 billion loan guarantee to stabilize JLR and prevent a wider collapse across the auto supply chain. The move underscored the national significance of the crisis. A major industrial powerhouse was brought to a halt by a few lines of malicious code, not by a strike or a lockdown.
But the biggest shock was the one JLR didn’t see coming. According to multiple reports, the company hadn’t secured a cyber-insurance policy before the breach. That meant its parent company, Tata Motors, had to shoulder the full cost of the downtime, the cleanup, and the damage to its reputation.
JLR’s oversight was far from unique. Many companies still treat cyber insurance as a formality rather than a financial safeguard. The JLR breach changed that perception. When a cyberattack can halt global operations for weeks, insurance becomes a critical tool for survival, not a box to check.
Threat-intelligence firms later pointed out that JLR employee login details had been spotted on the dark web months before the attack, possibly linked to a group called HELLCAT. Other analysts suspected a weakness in the company’s SAP NetWeaver software, which manages its logistics and manufacturing.
While neither claim has been officially confirmed, they point to a much bigger issue: modern factories are so interconnected, managed by so many vendors, and integrated with so many cloud services that they have a massive, open attack surface that most companies simply don’t understand.
By late September, JLR began getting systems back online and restarting production. But the story had changed. It was no longer about a “breach response” but about “business survival.” Other companies took notice. The JLR hack showed them that:
● Cyber is an operational risk. When a factory stops, cybersecurity and supply-chain management become the same thing.
● Third-party risk is everywhere. The more you outsource your IT, logistics, and cloud services, the more you expose yourself.
● Insurance is crucial. Not having coverage can turn a fixable breach into an end-of-days scenario.
● Government bailouts are not a plan. They might stabilize the market, but they can’t restore trust or prevent the next attack.
For investors and board members, JLR’s crisis marked a turning point. Cybersecurity was no longer seen as a cost center but as part of a company’s core value proposition. Manufacturers can no longer rely solely on financial metrics; they must also assess the digital dependencies woven throughout their supply chains. When a single breach can halt production and force a government bailout, cyber resilience becomes a defining measure of corporate strength.
By October, production had resumed. But a brand built on control and reliability had been humbled. JLR’s recovery will likely shape the future of automotive cybersecurity, where uptime, trust, and insurance are just as strategic as horsepower. To paraphrase one UK security analyst, the breach didn’t just shut down systems, it revealed how modern manufacturing runs on invisible code. When the code stops, so does everything else.
Why We Stopped Tuning and Started Coding: The Engineering Revolution in Detection
The evolution of cybersecurity from reactive defense to proactive engineering is best encapsulated by the rise of Detection Engineering (DE). This specialized discipline is now defined by the adoption of software development rigor, moving past the limitations of traditional, primitive security rules. This transition is essential because the current security landscape is plagued by systemic inefficiency: organizations report they cannot validate the majority of their existing detections, contributing to a dangerous average threat dwell times. This unreliability manifests as a massive operational constraint, consuming large amounts of team time in manually adjusting broken or ineffective rules, which also wastes significant financial resources on inefficient SIEM and logging queries.
The core solution is the methodology known as Detection as Code (DaC). DaC provides the scalable, systematic structure necessary to overcome this burden by treating detection rules, playbooks, and security workflows as version-controlled code artifacts. This practice enables automation, flexible deployment, and seamless integration into CI/CD pipelines, mirroring standard software development lifecycles. To ensure scalability and portability across disparate systems, DE relies on standardized formats like Sigma, the leading open-standard signature format (YAML) for expressing logic that can be deployed across tools like Splunk, Elastic, and CrowdStrike. The systematic use of DaC ensures the stability and efficiency of the detection program, freeing engineers to develop new capabilities rather than perform manual maintenance.
Effective DE requires the discipline of a Test-Driven Deployment (TDD) approach and must be fundamentally intelligence-driven. Detection logic is built using the specific tactics, techniques, and procedures (TTPs) of known adversaries, with the MITRE ATT&CK framework serving as the industry standard blueprint for mapping and prioritizing organizational coverage. However, while MITRE mapping is essential, it is purely theoretical and does not confirm whether underlying rules are actually working. For this essential validation, sophisticated DE relies on Purple Teaming—a collaboration between offensive (Red) and defensive (Blue) teams—to enhance rule accuracy. Many practitioners now view traditional Breach and Attack Simulation (BAS) as the wrong tool for validating individual rules, finding it to be over-engineered, manual, and incomplete for this task, as it often fails to provide insight into why a rule failed or if log dependencies and schema alignment are healthy. A superior, purpose-built approach to continuous validation focuses on checking rule health and log data integrity first, then layering TTP mapping on top to provide accurate coverage context, with a future path toward integrated, holistic “unit tests for detections” using lightweight adversarial emulation.
The commitment to DE is highly stratified by organizational size and resource maturity. Large enterprises focus on achieving high DE maturity through internal, dedicated DE teams, often positioned as a specialized group within Security Operations. Their investment targets core platforms and the strict internal implementation of DaC practices. Conversely, for the mid-market and Small-to-Midsize Businesses (SMBs), internal DE capabilities are often impractical due to staffing limitations and the persistent global talent shortage. For these segments, the strategic imperative is the adoption of Managed Detection and Response (MDR), which provides qualified professionals for outsourced threat hunting and response (SOC-as-a-Service), effectively democratizing high-maturity DaC capability.
The future of Detection Engineering over the next three years is inextricably linked to Artificial Intelligence (AI) integration. Many organizations are testing or planning projects to add AI powered solutions now, with the strategic goal of deploying AI/ML algorithms to automatically generate and optimize DaC rules, thereby transforming the manual tuning burden into autonomous optimization. Crucially, customers are demanding Explainable AI (XAI) to ensure transparency and auditability, explicitly rejecting “black-box” systems that historically generate false positives. This shift requires a corresponding evolution in the DE talent profile: the role is formalizing into a hybrid DevSecOps function, mandating proficiency in core software development practices, including version control and CI/CD pipeline management, to maintain and scale this automated defense environment. Ultimately, the ability of organizations to standardize their security logic through DaC will be the single most critical factor determining how effectively they can adopt and leverage future autonomous AI defense mechanisms.
A Phish, a Worm, and One Very Bad npm Week
In September 2025 the JavaScript ecosystem got an abrupt reminder of why open-source dependency hygiene matters. First came a straightforward but damaging account compromise that trojanized 18 widely used npm packages. A few days later security teams uncovered a clever, self-replicating worm that used build systems, security scanning tools, and GitHub Actions to harvest credentials and spread them across repositories. Both incidents show that attackers are no longer just trying to slip bad code into a library. They are targeting the people and processes that produce libraries.
The first incident began with social engineering. An attacker phished the npm account of a prolific maintainer and published malicious versions of chalk and debug. Those utilities collectively see billions of downloads and are woven into countless builds, so one compromised account instantly put huge parts of the ecosystem at risk. The injected payload was obfuscated JavaScript intended to intercept and redirect cryptocurrency transactions in browser contexts. The malicious versions were removed, but the damage had already rippled outward and required coordinated rollbacks and cache purges.
The second incident, labeled Shai-Hulud by researchers, worked very differently. Malicious packages, when installed, ran lifecycle hooks that scanned for secrets such as GitHub tokens, npm publish tokens, and cloud credentials. The code exfiltrated the secrets it found, then used them to publish new malicious versions or to inject workflows into CI pipelines. The worm’s cycle: Install, steal, republish. This design turns build systems and downstream libraries into propagation vectors. Reports show hundreds of packages and many infected versions were discovered within days. Vendors and researchers have published detailed analyses of the worm’s mechanics and the signals defenders should monitor.
These two attacks are important beyond the immediate headlines. Software supply-chain attacks have been a known risk for years, but these examples show the next level of threat: attackers are abusing collaboration and automation themselves. The first incident targeted a high-profile contributor, which gave the attacker an outsized publishing surface. The worm weaponized automation and security tools so it could automate exfiltration and spread. There is a bitter irony here: tools meant to keep code safe were co-opted to steal secrets.
So what should we do? The usual hygiene advice remains true. Phishing-resistant MFA and least-privilege access control help and should be mandatory. But hygiene alone is not enough. The core problem is artifact governance and distribution control. Open source thrives on sharing and self-organizing collaboration, and attackers are finding ways to exploit that openness. We need incentives and shared practices that encourage not only collaboration on functionality, but also collaboration on protection. Teams should be able to see how hardened a library version is before they consume it.
Some organizations are already building parts of the solution. Sonatype and JFrog are strong in artifact governance and repository controls. Chainguard publishes a hardened catalog of open-source images. OpenSSF Scorecard and GitHub Allstar help rate and enforce repository hygiene. One of our portfolio companies, Strider, recently released OSS Search to give visibility into contributor populations and signals of potential nation-state influence. These approaches matter, but they do not solve the problem by themselves. We need more startups and open-source projects innovating on provenance, attestation, behavioral detection, and developer protection.
The September incidents are another reminder that attackers will keep inventing new ways to subvert the supply chain. From the 2018 event-stream compromise to the 2024 XZ Utils backdoor and now the 2025 npm attacks, the pattern is the same: attackers exploit trust, automation, and mass distribution to maximize impact. With estimates that open-source components make up roughly 90 percent of modern software, the stakes are high. The industry must push harder on technical and governance solutions. The practical path forward is layered controls combined with transparency and shared attestation, so collaboration continues to accelerate software rather than accelerate compromise.