Cyber Trends & Predictions for 2025


We are fortunate to meet so many unbelievably motivated and talented founders. Through the DataTribe Challenge, as well as throughout the year, we see a lot of ideas. Since a seed-stage startup usually takes 7 to 10 years to become a market leader, the stream of super early-stage startups offers a glimpse over the horizon. Since founders quit jobs and often put their own money on the line, startups represent high-conviction bets placed by deep domain experts. This is all to say that our deal flow provides a unique market signal and, thus, a useful crystal ball. So, once a year, we like to reflect on surface themes and trends we are seeing.
We also have the pleasure of working closely with the CEOs of our portfolio companies and the CISOs in our CISO Network. All these folks are experts with deeply-informed points of view on different aspects of cybersecurity. So, in looking ahead into 2025, we also wanted to know what is on the minds of our CEOs and CISOs. To find out, we asked them for their top prediction for 2025 and have included those here as well. We’re grateful to these busy folks for sharing their perspective with us.
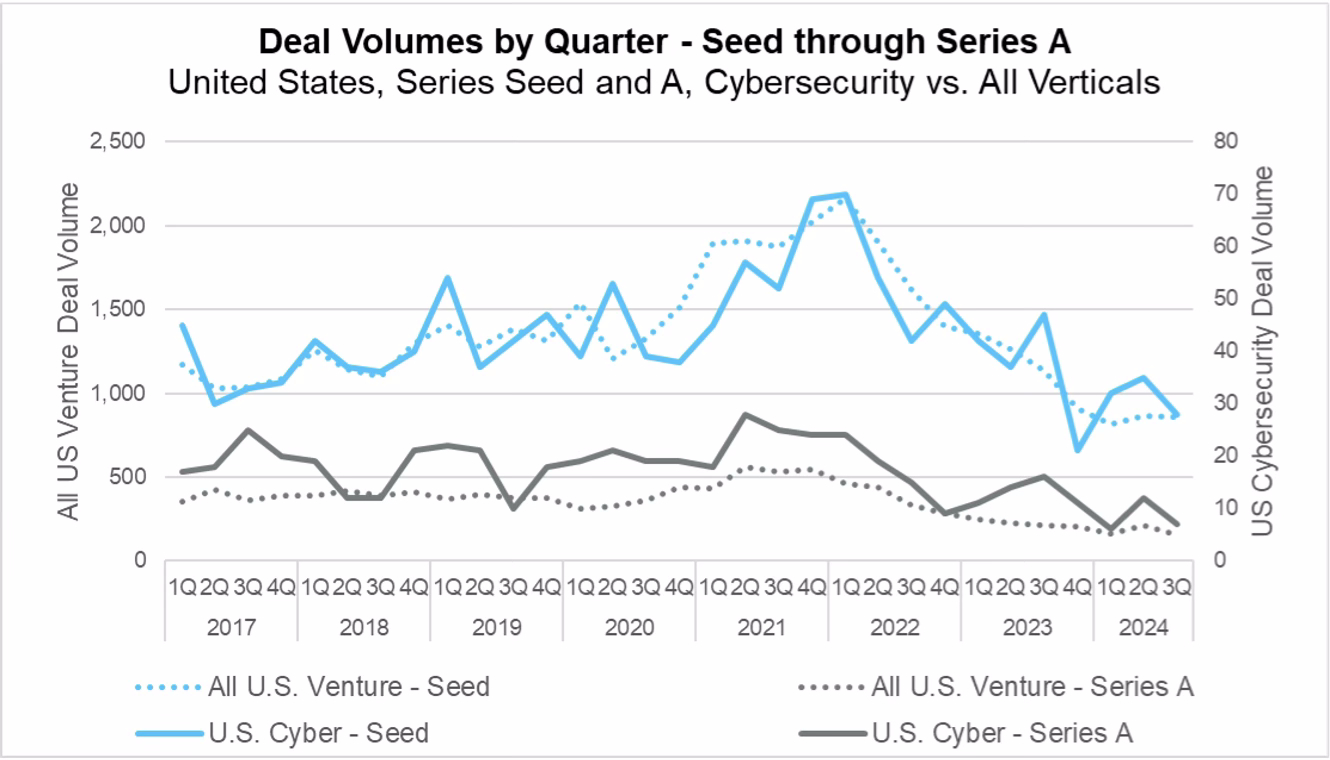
Venture investment deal counts in cyber were lower in 2024 compared to 2023 but have shown signs of leveling off as COVID-era exuberance and tourists have pulled back. Though down, cyber remains active, with invested capital on track to end the year slightly higher than 2023 and to exceed pre-Pandemic 2020 levels.
With major elections happening in 64 countries this year and the most voters going to the polls ever, election security was in the air this year. Regarding major cyber incidents, 2024 delivered plenty to keep the industry on its toes. We’ll remember 2024 as the year that a Chinese threat actor attempted to backdoor Linux through XZ Utils and 40% of US medical claims processing stopped working when Change Healthcare went offline due to a cyber-attack, 8.5M computers were bricked when CrowdStrike issued a flawed update providing a preview of what cyberwarfare might look like when a breach of Snowflake resulted in data loss on hundreds of millions of customers across 165 organizations include Ticketmaster, Santander Bank, and AT&T, and when Chinese threat actor Salt Typhoon compromised telco systems in Verizon, AT&T and T-Mobile giving them the ability to wiretap any mobile phone in the U.S. As we look ahead to 2025, we hope the industry will continue to internalize lessons from prior incidents to build resilience and raise costs for our adversaries. And, of course, 2024 was the year when all that AI that splashed across enterprises in 2023 started to seep in – creating both opportunities and threats.
As we all set forth into 2025, these are the areas where we are seeing new company formation in cybersecurity.
10. Cybersecurity ROI Management: Helping CISOs hack budgets. CISOs face growing challenges with tool sprawl and rising costs as they navigate an ever-evolving threat landscape and a steady influx of solutions targeting the continually changing enterprise attack surfaces. In a world where robust cyber defense is critical for business continuity, CISOs must balance adopting new tools with controlling budgets. Maximizing ROI on existing platforms and seamlessly integrating new solutions is a top priority. Startups are stepping in to help, leveraging industry best practices and industry-wide software purchase data, combining business and IT risk context, active threat intelligence, and quantitative analysis of security operations to buy down risk optimally.
9. AI-Powered Security Verification and Testing: When it comes to software security, AI is rewriting the script on debugging. AI seems part of every conversation today, and software security testing and verification are no exception. Recently, many startups have been building AI-driven solutions, from high-volume intelligent fuzzing to processing telemetry data from software in test or production environments. These advancements enable identifying and mitigating high-risk operations, sometimes even blocking them in real time. As society becomes increasingly reliant on software, its reliability is paramount. Despite robust testing, human error and the complexity of modern software nearly guarantee that some vulnerabilities will escape detection and reach production. However, with AI dramatically enhancing testing capabilities, development teams now have a better chance to release more reliable software with fewer vulnerabilities.
8. Hardened Operating Systems & Containers: Because system failure is not an option when it comes to life and death. The world’s digitization demands that application software run smoothly and that the underlying systems—databases, communications, operating systems, firmware, and hardware—function flawlessly. Whether in medical devices, automobile components, or traffic control systems, these technologies often control operations where failure can mean life or death. This raises the bar for trustworthy operation. Startups are innovating new methods to ensure the reliability of these systems, from formal verification that mathematically proves key requirements are met to infrastructure-as-code testing and automated scanning that generates trustworthy containers and system configurations. These efforts help harden the foundational layers of the technology stack. Trusting these lower layers is essential when assessing risks in a product’s end-to-end software and hardware bill of materials (SBOM and HBOM).
7. Next-Generation Identity & Identity Security Posture Management: Securing the new identity landscape. The identity landscape for the modern enterprise has shifted drastically in the last few years. Non-human identities have surged, organizations have embraced cloud-native environments, and artificial intelligence has shifted how identities are managed. As this landscape evolves, startups have stepped in to create the next generation of identity management, providing just-in-time access, continuous authentication, and AI-based anomalous access detection.
6. Ransomware Defenses: Dedicated defense against headline-grabbing attacks. Ransomware attacks and payments reached record levels in 2024, with the average ransom reaching $2.73 million during the year – up more than $1 million from 2023. As the threat of ransomware continues to rise, several startups have stepped in to provide dedicated solutions. These companies take a multi-faceted approach, targeting ransomware before execution, attempting to intercept decryption keys, backing up data, and preventing its exfiltration. This in-depth defense approach provides security even as evolutions in ransomware allow it to bypass individual controls.
5. Data Security & Management: Securing data in an increasingly complex environment. The amount of data stored by enterprises is growing exponentially, stored in hundreds of disparate locations, accessed by countless applications, and subject to a growing number of regulations. In such a setting, it is no surprise that innovators have entered the market, seeing opportunity in the chaos. Many companies see this environment as a natural fit for artificial intelligence, using it to discover, catalog, and redact data to enforce compliance. Others have focused on the governance of data flows, creating visibility into where and how data is used, and ensuring the prevention of data leaks and compliance issues in real-time.
4. Machine Identity Management: Digital ecosystems are no longer predominantly human. The number of non-human or machine identities has drastically increased in recent years. These machines comprise nearly the entirety of an enterprise’s IT infrastructure, encompassing physical devices, such as desktops or IoT devices, and workloads, such as applications or containers. Given the importance of these machines to IT operations, it is clear why securing their identities has become a top priority for security teams. Naturally, startups have rushed in to meet this need, offering continuous discovery and inventory of credentials, lifecycle management, and constant auditing to ensure the least privileges are granted to each machine.
3. Securely Adopting AI Applications: Is it a discreet consigliere or a loose-lipped gossip in your pocket? One of the most palpable feelings when departing from the RSA Conference in 2024 was that there was a chaotic rush to adopt AI applications happening all across businesses everywhere; it was a free-for-all, and CISOs were struggling to keep up with controls. With the almost magical power and simplicity of ChatGPT, many well-meaning folks everywhere, just trying to get their jobs done more efficiently, are using LLMs for all sorts of tasks. Few understand the potential risks to sensitive organizational information. While putting controls in place to enable the benefits of LLMs while reducing risks is similar to existing data management challenges, there is enough difference in the patterns of behavior and the data used to create significant new requirements (and opportunities for entrepreneurs).
Of course, LLMs are not just used by end users through chat-based assistants. LLMs are being incorporated into SaaS products and built into home-grown systems. So, security teams also need to pay attention to their data as it flows into other systems that are now leveraging LLMs. This will remain a prominent theme for the next few years as the broad-based adoption of LLMs washes over enterprise computing.
2. Deepfake Risk Mitigation: A risk from the future arrives in the present. In January of this year, a political operative created a deepfake of Joe Biden to persuade thousands of voters to skip the New Hampshire primary. In May, an audio deepfake resulted in a Hong Kong-based engineering firm wiring $25M to fraudsters. In July, a North Korean hacker passed four video-based interviews to get hired by cybersecurity training firm KnowBe4. The hacker was soon discovered when he started loading malware onto the company network using the laptop the company issued him. In September, Senator Ben Carden engaged in a Zoom call with someone purporting to be the former Ukrainian Foreign Affairs Minister. It wasn’t until “the Minister” posed strange questions that Carden became concerned, disconnected from the call, and reported it to the State Department.
Deepfake technology is not new. Nor is the concern for the potential misuse of deepfakes new. However, with AI technology rapidly advancing and a record number of national elections this year, deepfakes accelerated into the mainstream. Entrepreneurs are responding. One of the most noticeable new trends in our deal flow this year has been the emergence of deepfake risk management startups. In fact, not one but two of the Finalists in this year’s DataTribe Challenge were deepfake-related. From authenticating people on video calls to broad-based content authentication systems that are integrated directly with cameras and social media platforms to the emerging standards from the Coalition for Content Provenance and Authenticity (C2PA), deepfake management is an area to watch in 2025.
1. Autonomous Security Operations: Agents will help close the cyber labor gap. Security operations centers (SOCs) receive thousands of alerts daily. Many of these are false positives. Sifting through the alerts is demanding work that requires skill. Companies have struggled to keep up with the need for cyber professionals. There’s an estimated global cybersecurity workforce gap of 4.8 million workers. You’d need to almost double the current 5.5M global workforce to fill that gap. To say there is a big demand for cybersecurity talent is an understatement.
Given that one of security analysts’ primary activities is to analyze security alerts, drill into data, and identify patterns of anomalous behavior, security operations is a natural for AI. The AI SOC Analyst and autonomous security operations emerged as a significant new trend last year and remain prominent this year. This year, the term “agentic” has bubbled up as automation is increasingly framed in terms of “agents.” We’ll continue to see AI automation in security operations in the coming years as agents absorb work that has been overloading humans. This will be as common as SIEMs.
Our analysis of emerging trends in cybersecurity would be incomplete if we didn’t touch briefly on the potential impacts of the change of the U.S. presidential leadership. While there has been much national discourse about what changes we can expect as the President-elect looks to enact his policies, cybersecurity is one area where there has been very little guidance. In many ways, cybersecurity holds a unique spot in politics. It is one of those rare areas that largely benefit from bipartisan support, ensuring cybersecurity remains prioritized at the national level.
President Trump’s first term as President was marked by significant progress as the administration enacted several policies that included an executive order for modernizing IT infrastructure within the US government, the creation of the Cybersecurity and Infrastructure Security Agency (CISA), the evaluation of the U.S. Cyber Command, and the first national cybersecurity strategy in 15 years. Many of these trends were continued under President Biden’s administration, with notable progress in disrupting cybercriminal operations domestically and abroad and looking to implement “secure by design” principles in software development.
Despite the bipartisan support cybersecurity has enjoyed over the last decade, there are several areas to watch as the new administration gets sworn in two months.
No area of cybersecurity has been more bipartisan than critical infrastructure, a trend we expect will continue with the incoming administration. Under the Biden Administration, and in response to high-profile attacks such as the 2021 Colonial Pipeline ransomware attack, there has been a strong push to roll out sector-specific regulations to increase overall security. While these regulations have seen success in areas such as railroads and aviation, they have also seen legal setbacks in areas such as water and healthcare; these challenges could increase in the wake of the Supreme Court striking down Chevron and limiting the authority of federal agencies.
While the incoming Trump administration is likely to continue focusing on critical infrastructure, especially given its importance in geopolitical conflicts with China, Iran, and Russia, it is most likely that they will look to decrease overall regulation and try and work with utilities and businesses to create more streamlined and informed policy focused on creating incentives as opposed to legal risk.
Despite signing the legislation that created the Cybersecurity and Infrastructure Security Agency (CISA) in 2018, President Trump has not always been the biggest fan of the Agency he created. Back in 2020, Trump fired the first director of CISA Chris Krebs, when he stated that there was no evidence that the 2020 elections had been tampered with. Under Biden, CISA has taken a more active role in critical infrastructure and misinformation accountability, actions that have been under fire from Republicans since 2022.
It has already been announced that current CISA director Jen Easterly will be stepping down in the coming months, and there will be new leadership at the nation’s leading cybersecurity agency; it is expected that the new leadership will align with the incoming administration’s public comments and look to scale back the scope of CISA. This could affect initiatives around “secure by design” and legal liability for software vendors who ship software with vulnerabilities.
As with critical infrastructure, there is expected to be a general rollback of regulation in the overall cybersecurity space. One high-profile area that could be the first to see significant change is AI, specifically the repeal of President Biden’s executive order on AI. The executive order, signed in October of 2023, required companies to provide more reporting on foundation models’ development, training, deployment, and capabilities to ensure that security and areas such as bias were being reviewed.
Overall, we have heard very little directly from the Trump administration about their cybersecurity strategy and priorities for Jan 21st. Based on what we know from 2016-2020 and the overall rhetoric coming from those surrounding the administration, it’s clear that areas such as critical infrastructure and national security will continue to be a top priority and that Trump and his appointees will look to reduce regulations and scale back the authority of agencies such as CISA.
“The gains of Offensive AI in experimental targeting of “key persons” we saw in the election will be transformed into attacks on/using “key persons” at our nation’s largest companies in 2025 and beyond.” – Chris Pierson, CEO & Founder, BlackCloak
“I think we’ll see two things in 2025. Attackers will begin to shift from traditional ransomware campaigns as governments make it harder to pay and insurance carriers reduce coverage for those specific events. For defenders, I believe we’ll continue to face stronger than usual budget constraints, most likely until the Federal Reserve reduces interest rates and markets open up more. This will force a lot of folks to make some big risk-based cuts to their cybersecurity programs, taking more risk where they may not have before.” – Chris Castaldo, CISO, Crossbeam
“While the promise of AI remains substantial, its value is rooted in an organization’s ability to access and utilize rich, relevant data for evaluation and training. This core need will be abundantly clear as AI tools move from sandboxes to operational environments with much higher stakes. For cyber leaders, this will also amplify the need to ensure that data sources can be used in a manner that prioritizes both security and privacy. If not, the value business and mission value delivered by AI will be unable to overcome the impact of risks it introduced.” – Ellison Anne Williams, CEO & Founder, Enveil
“AI helps defenders find ODays before the attackers do.”– Diana Kelley, CISO, Protect AI
“It’s the beginning of the end for SBOM. The industry will acknowledge that nobody uses them and they don’t solve anything.” – Michael Edenzon, CEO & Co-Founder, Fianu
“Increased market demand for tools which enable an organization to effectively monitor and quantify the risk of GenAI/LLM deployed within the organization’s ecosystem and across its third parties.” – Dan Sadler, CISO, Constellation
“In 2025, you will see insurance companies and corporations turning away from single score/rating methods for evaluating cyber security readiness. Insurance companies will increasingly develop proprietary methods to more accurately and quickly rate customers. Corporations focused on third-party risk will also leverage proprietary methods and third parties (like SixMap) to assess the risks of doing business more accurately. Short any company whose business is reliant on selling security ratings.” – Jason Kaplan, CEO SixMap
“AI in 2025 will transform cybersecurity, driving both advanced threats like deepfake-powered social engineering and hyper-personalized attacks, and revolutionizing cyber defense with predictive, AI-driven threat detection and automated responses. While cybercriminals exploit AI’s precision and scalability, defensive systems will evolve to contain threats faster and more effectively than ever before, though adoption by CISOs may prove to be slow and cautious.” – Jeff Brown, Customer Security Officer, Microsoft
“Many CISOs will leave Splunk and QRadar and look for data lakes, and detection engineering platforms will be the new solution on top of a data lake.” – John Bruns, Global CISO, Anomali
“Although Cybersecurity AI is the latest buzzword in the infosec bingo game, Infosec professionals will soon learn that “Using AI” is not a strategy. “Using AI” is a tactic. It’s a potential tool at your disposal. It may help reduce the probability of material impact to your organization, but there is no guarantee. Just because you deploy a tool that uses AI to provide a service or build one yourself doesn’t mean it will automatically buy down risk. Automation is a strategy, and “Using AI” might be a tactic we deploy. But it’s expensive in terms of backend costs to be proficient at using it. “Using AI” has much potential, but it’s not free. It will take investment in the entire people-process-technology triad from both the vendor and the user perspective. As an infosec professional, I’m looking for a tool that buys down the risk to my organization, not a tool that uses AI because it has made it to the top of the Gartner Hype Chart.” – Rick Howard, CSO, N2K Networks
“CISO as Business Process Executive.” – Tom Quinn, T. Rowe Price